Worms Observed in the Honeynet
Updated 12/10/2003

Rise of MSBlaster (also see this and many other references) on a nice wormy day of August 11. An ominous sight to behold indeed... Note an interesting and largely unexplained trail preceding the actual outbreak. The worm exploits this DCOM vulnerability in Windows
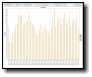
How is CodeRed doing nowadays? Pretty well, it seems. The plot above shows the CodeRed related event counts in our honeynet for the last couple of months. Will it ever die? Nobody can say for sure, but it doesn't look likely. July 2001 feels like last century, but CodeRed is here with us. Some say its the "script kiddies" trying to sneak under the noise, but I doubt that. CodeRed should have eliminated most of the vulnerable and exploitable boxes... The data might contain a small mix of CodeRedII.

Rise and fall of the mighty Slammer in January 2003 (some fun research on Slammer propagation is here). This plot looks more like the "fall of Slammer", this is due to the fact that its rise was SO dramatic so it is only shown by one bar. Then, as congested networks went down and folks patched boxes or blocked outbound flooding, the rate went down. The worm exploits this vulnerability.
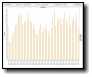
Slammer today. Still alive and well, "slamming" MS SQL database all over the place. The data matches up with what DShield sees.
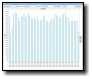
Welchia, from a DCOM worms family. Now this one is real noisy today! Check out the event counts from my honeynet for the tell-tale sign of Welchia - Snort Cyberkit 2.2 signature.
Anton A. Chuvakin
Last modified: Tue Dec 06 22:57:57 Eastern Standard Time 2005